Global Technologies & Services
Providing innovative industry solutions and services worldwide
Technology Solutions and Services
Contact us for a free consultation or to find out more about how our products and services can help enable your business.
The Templar is a ruggedised, eco-friendly Mobile Data Centre designed for Governments, Critical National Infrastructure (CNI) organisations, businesses and individuals.
The Templar provides access to a fully portable rapid deployment capability for business-critical ICT. Weighing just 15 kgs and with a myriad of uses, from secure data back-up to a mobile headquarters, The Templar is customisable to specific security needs. It can be deployed worldwide on demand to provide cutting edge communication and data processing with automated set up in minutes.
Use cases include:
- Emergency Response/Disaster Situations;
- Business Continuity;
- Military Deployment;
- Backups.

Organisations are being exposed to new threat vectors as networks face increasing vulnerabilities. Templar BLADE provides actionable insights which proactively address these vulnerabilities and protect your business.
Templar BLADE (Business-Level Assurance Diagnostic Engine) is a unique data mining intelligence service used by FTSE 100 and 350 companies, High Net Worth individuals and others, to obtain and review actionable intelligence from covert as well as open sources on the internet, including the dark web and social media.
BLADE Light is an innovative offering for small and medium sized organisations to quickly and cost-effectively identify vulnerabilities within your networks, devices and systems. At a time when hybrid working is becoming the new norm, the results will allow your organisation to rapidly identify, prioritise and remediate any issues that are exposed.

Cyber Physical Security Services

Cyber-physical security addresses security concerns for physical systems used to maintain and implement cyber security solutions and services, including Internet of Things, operational technology, and industrial control systems. We help organisations mitigate cyber and information risk through physical protection of infrastructure / cyber assets and the cyber protection of physical assets.
Identity Risk Management & Deception Technologies
Digitalisation and the growing convergence of OT/IT is manna from heaven for attackers, deploying ransomware against an ever expanding Cyber-attack surface. Addressing endpoint complexity and risk requires a dynamic and proactive response. Illusive’s Active Defence is an innovative approach enabling organisations to deploy a diversified detection strategy and creating a hostile environment for attackers.
Illusive’s Active Defence Platform is a threat detection and deception technology that finds vulnerabilities and remediates them and then creates a false expanded attack surface to identify and contain threat actors.
The Active Defence Platform consists of three main solutions:
- Attack Surface Manager;
- Attack Detection System;
- Attack Intelligence System.

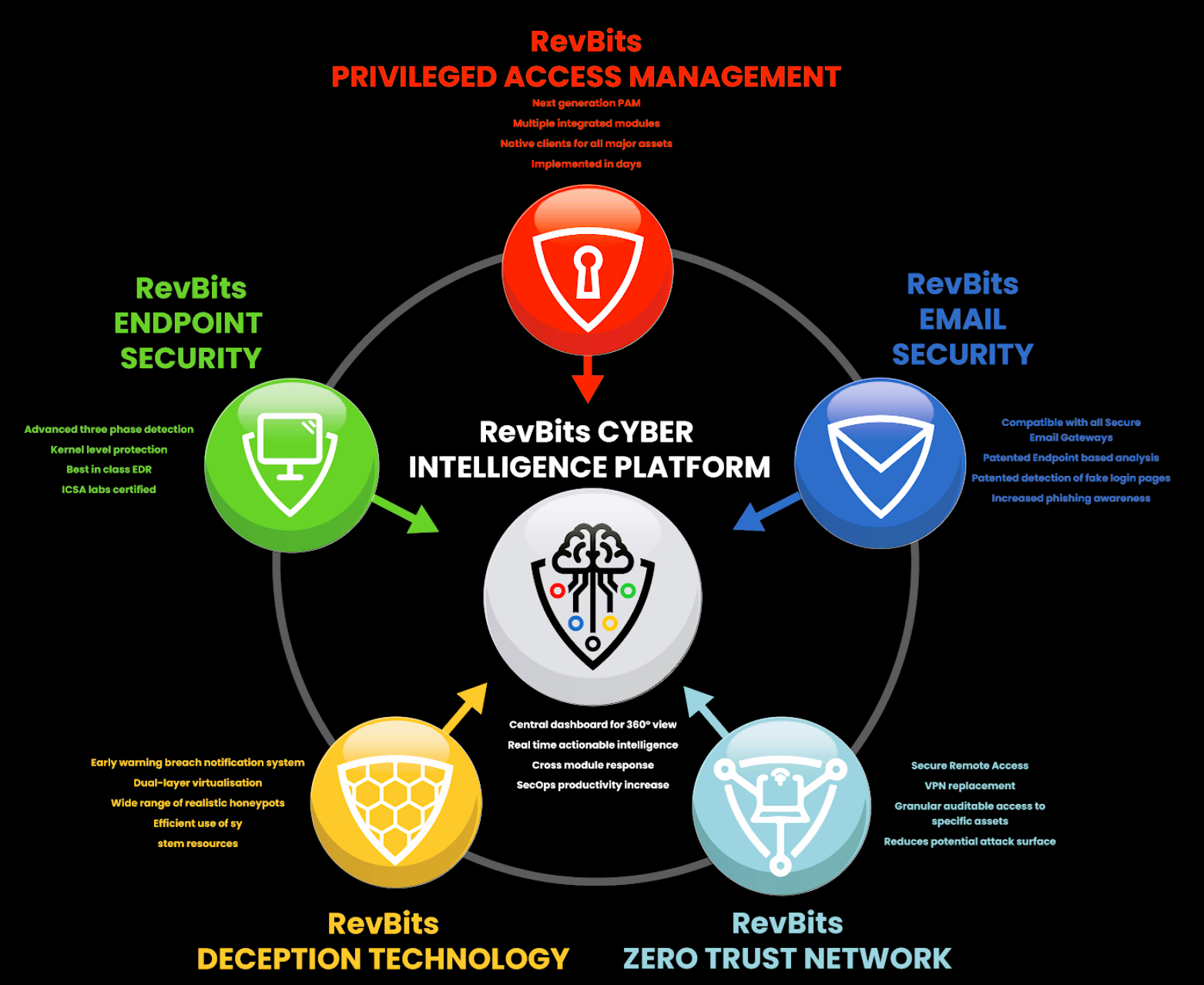
With the threat landscape continuing to grow rapidly, it is crucial organisations are prepared to defend against different attackers and techniques across the entire enterprise. RevBit’s innovative software can be used in all environments, including on-premise, Hybrid or SaaS and is designed to address this challenge with solutions including:
- Cyber Intelligence Platform CIP/XDR provides a single sign-on custom-built unified analytics dashboard to integrate and manage RevBits modules for cross-platform alert notification and actionable intelligence.
- End Point Security (EPS/EDR) conducts a three-phased analysis on new executables and includes a comprehensive and robust EDR solution. Patented technology affords visibility and operation at the kernel level.
- Email Security provides endpoint algorithmic analysis, capturing and blocking the ‘miss rate’ of complex and sophisticated multi-layered phishing emails (patent) and page impersonation attacks. Compatible with all secure email gateways (SEGs).
- Zero Trust Networking (ZTN) replaces incumbent VPNs, offering Secure Remote Access. Granular and fully auditable access is provided to specific business critical assets.
- Privileged Access Management (PAM) a comprehensive multi-modular access management solution. Patented technology with maximum security, seamless high availability fail-over and rapid implementation make this a comprehensive Next Gen PAM solution.